The security of data on networks is an ever-growing concern in today’s digital landscape. As cyber threats continue to evolve and become more sophisticated, the need for robust encryption methods to protect sensitive information has never been greater. In this article, we will delve into the best practices for encrypting data on networks, equipping you with the knowledge and tools necessary to safeguard your valuable data assets.
Expect to uncover insightful strategies for implementing encryption tools, understanding different cyphering methods, and enhancing your network’s overall security posture. By the end of this article, you will be empowered with actionable steps to strengthen your data protection measures and fortify your network against potential breaches. Let’s embark on this journey together towards a safer and more secure digital environment.
Understanding the importance of data encryption
Data encryption is akin to placing your valuable information in a safe box with an intricate lock. In today’s digital age, where cyber threats lurk around every corner, protecting data is paramount. Encryption ensures that sensitive data remains confidential and secure, shielding it from unauthorized access and potential breaches.
By encrypting data on a network, you are essentially transforming it into an unreadable format through complex algorithms. This process converts plain text into ciphertext, making it incomprehensible to anyone without the decryption key. Without encryption, sensitive information such as passwords, financial details, and personal communications are vulnerable to interception and exploitation by cybercriminals.
Furthermore, data encryption not only safeguards confidentiality but also upholds integrity and authenticity. It verifies that the information has not been altered during transmission or storage. This integrity check ensures that the data received is the same as what was sent initially, instilling trust in the accuracy and reliability of digital communications.
In a world where data breaches are increasingly common, embracing robust encryption practices instills confidence in both businesses and individuals. It demonstrates a commitment to cybersecurity best practices and assures stakeholders that their information is being handled with the utmost care and diligence. Understanding the significance of data encryption sets a strong foundation for building a secure network environment.
Getting Started with Encryption Tools
Choosing the Right Encryption Tool: Selecting an encryption tool is crucial for securing your network data. Consider factors like compatibility with your systems, ease of use, and level of encryption offered. Popular tools include VeraCrypt, BitLocker, and AxCrypt.
Installation and Setup: Once you’ve chosen an encryption tool, follow the installation instructions carefully. Set up passwords or key files to access encrypted data. Create a backup plan for your encryption keys to prevent data loss in case of emergencies.
Understanding Encryption Algorithms: Familiarize yourself with different encryption algorithms such as AES, RSA, and Blowfish. Each algorithm has unique strengths and weaknesses in terms of speed and security. Choose the algorithm that best suits your network’s needs for optimal protection.
Training and Education: Invest time in learning how to effectively use your chosen encryption tool. Attend training sessions or online tutorials to enhance your knowledge of encryption best practices. Stay updated on new developments in encryption technology to stay ahead of potential threats.
Exploring Different Encryption Methods
When it comes to securing data on your network, exploring different encryption methods is crucial. One common method is symmetric encryption, where the same key is used for both encryption and decryption. This method is fast and efficient, making it ideal for encrypting large amounts of data.
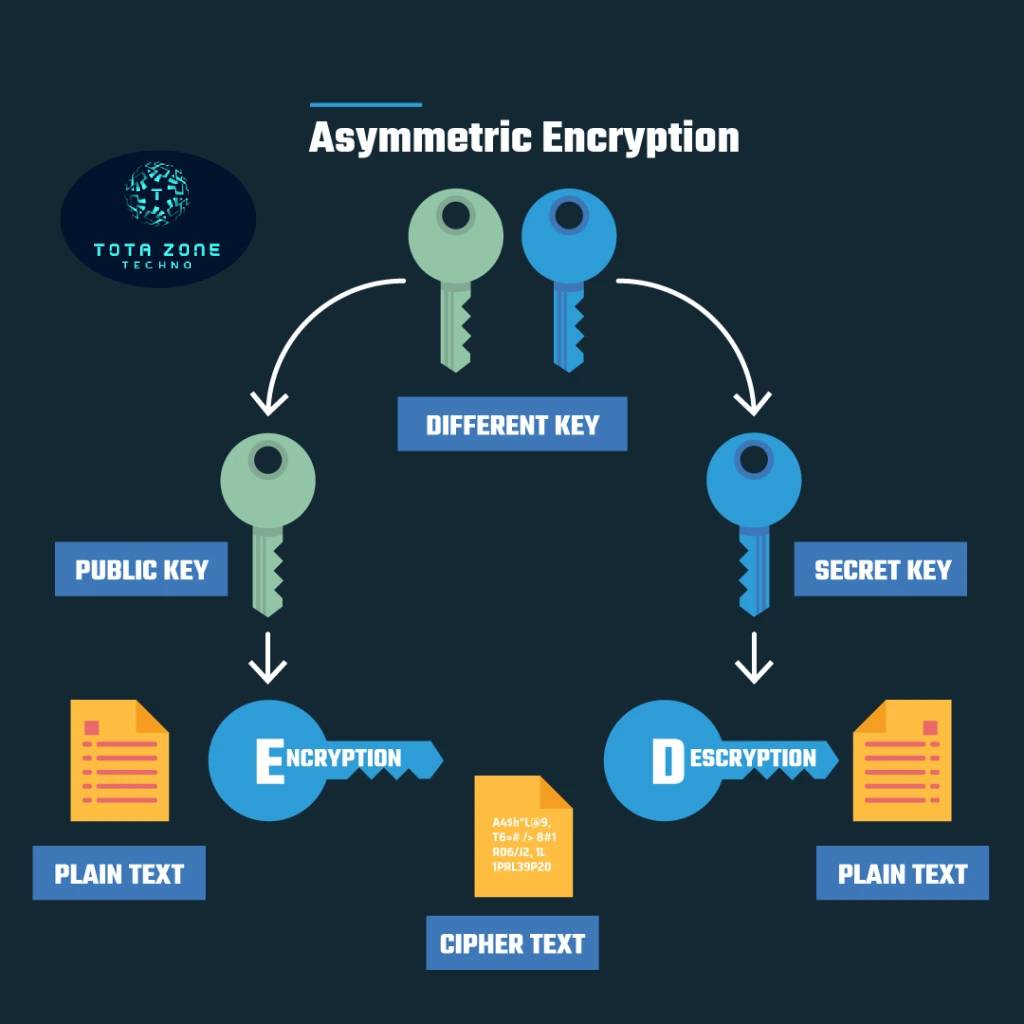
Asymmetric encryption, on the other hand, uses a pair of keys – a public key for encryption and a private key for decryption. This method is more secure than symmetric encryption but can be slower due to the complexity of managing key pairs. It is often used for secure communication over networks.
Another popular encryption method is hashing, which converts data into a fixed-length string of characters. While not reversible like encryption, hashing is commonly used to verify data integrity and securely store passwords. It provides an added layer of security in combination with other encryption methods.
Furthermore, quantum cryptography is an emerging field that leverages the principles of quantum mechanics to create unbreakable cryptographic systems. Although still in its early stages, quantum cryptography shows great promise in revolutionizing data security by utilizing quantum properties such as entanglement and superposition.
Tips for Creating Strong Encryption Keys
Randomness is Key: When generating encryption keys, ensure they are truly random to prevent predictability. Utilize specialized tools or algorithms that can create high-quality random data. Remember, the strength of an encryption key heavily relies on its randomness.
Length Matters: Increasing the length of your encryption keys enhances security. Opt for longer key lengths as they provide greater complexity and make it more challenging for adversaries to crack the encryption. Aim for industry-standard key lengths to bolster your data protection.
Diversify Your Keys: Avoid reusing encryption keys across multiple systems or sessions. Generate unique keys for different purposes and regularly update them to mitigate the risk of potential vulnerabilities or attacks. Diversifying your encryption keys adds an extra layer of defense against unauthorized access.
Maintain Key Confidentiality: Safeguard the confidentiality of your encryption keys at all times. Store them securely in a dedicated key management system or hardware security module (HSM) to prevent unauthorized access. By protecting the secrecy of your keys, you strengthen the overall integrity of your encrypted data.
Implementing data encryption on your network
Data encryption is a critical aspect of securing sensitive information on your network. Implementing encryption ensures that even if unauthorized users gain access to your data, they won’t be able to decipher it without the proper decryption key.
Choosing the right encryption algorithm
When implementing data encryption on your network, it’s essential to select the right encryption algorithm based on your security needs. Advanced Encryption Standard (AES) is widely considered one of the most secure and efficient algorithms available today, offering strong protection for your data.
Integrating encryption into your existing systems
To successfully implement data encryption on your network, you need to seamlessly integrate it into your existing systems and workflows. This requires careful planning and coordination with IT professionals to ensure that encryption doesn’t disrupt normal operations but enhances security instead.
Training employees on data encryption best practices
Effective implementation of data encryption also includes educating employees about best practices for handling encrypted information. Training sessions can help raise awareness about the importance of encryption, how to securely share encrypted files, and how to recognize potential security threats.
Securing data transmission with encryption protocols
Data transmission over networks is vulnerable to interception by malicious actors. Utilizing encryption protocols is vital in safeguarding sensitive information during communication. These protocols ensure that data is encrypted before being sent and decrypted upon reaching the intended recipient, preventing unauthorized access.
One of the most widely used encryption protocols is Secure Sockets Layer (SSL) or its successor, Transport Layer Security (TLS). These protocols establish a secure connection between a client and a server, encrypting data during transit. Implementing SSL/TLS ensures that communication remains confidential and protected from potential eavesdroppers.
Another essential encryption protocol is Internet Protocol Security (IPsec), which secures IP communications by authenticating and encrypting each IP packet within a session. With IPsec, data integrity and confidentiality are maintained across network connections, enhancing overall security for transmitted information.
Employing Virtual Private Network (VPN) technology also enhances data transmission security. VPNs create encrypted tunnels for data to travel through, shielding it from prying eyes. By routing traffic through secure servers, VPNs add an extra layer of protection to ensure confidentiality and integrity in network communication.
Monitoring and maintaining encrypted data
Ensuring the security of encrypted data is an ongoing process that involves vigilant monitoring and regular maintenance. By actively monitoring your encrypted data, you can quickly identify any unusual activity or potential security breaches, allowing you to take prompt action to protect your network.
Maintaining encrypted data involves regularly updating encryption keys, certificates, and protocols to ensure they are strong and up-to-date. This proactive approach helps mitigate vulnerabilities and strengthens your overall network security posture.
One effective way to monitor encrypted data is through the use of intrusion detection systems (IDS) and intrusion prevention systems (IPS). These tools can help identify suspicious behavior or unauthorized access attempts within your network, enabling you to respond swiftly and decisively.
Regularly conducting security audits and vulnerability assessments on your network can also help in maintaining the integrity of your encrypted data. By assessing potential weak points in your encryption implementation, you can address any issues proactively before they are exploited by malicious actors.
Best Practices for Data Encryption on Networks
Implementing best practices for data encryption is crucial in ensuring the security and integrity of your network. By following these guidelines, you can enhance the protection of sensitive information and mitigate the risk of cyber attacks.
1. Conduct Regular Security Audits
Regular security audits are essential to identify any vulnerabilities or weaknesses in your network’s encryption protocols. By conducting thorough assessments, you can proactively address any potential security gaps and strengthen your data protection measures.
2. Stay Updated with Encryption Standards
Stay abreast of the latest encryption standards and technologies to ensure that your network is equipped with robust security measures. By staying informed about advancements in encryption methods, you can adapt and enhance your data protection strategies accordingly.
3. Encrypt Data at Rest and in Transit
Encrypting both data at rest (stored data) and data in transit (data being transmitted) is paramount for comprehensive security. Utilize strong encryption algorithms to safeguard sensitive information whether it is stored within your network or being transmitted between devices.
4. Train Employees on Encryption Protocols
Educate employees on the importance of using encryption protocols correctly and securely within the organization. By providing training on best practices for data encryption, you empower staff members to actively contribute to maintaining a secure network environment.
Overcoming Common Challenges in Data Encryption
Ensuring data encryption is a vital aspect of network security, but it comes with its own set of challenges. Being aware of these common hurdles and knowing how to overcome them can significantly enhance the effectiveness of your encryption efforts.
Key Management
One of the most prevalent challenges in data encryption is proper key management. The complexity lies in securely generating, storing, and distributing encryption keys to authorized parties while safeguarding them from unauthorized access. Implementing robust key management practices, such as regular rotation and secure storage mechanisms, can mitigate this challenge effectively.
Performance Impact
Data encryption can sometimes lead to performance degradation due to the computational overhead involved in encrypting and decrypting data. To overcome this challenge, optimizing encryption algorithms and leveraging hardware acceleration can help improve performance without compromising security. Balancing between speed and security is crucial for maintaining efficient network operations.
Interoperability
When dealing with multiple systems or applications that use different encryption protocols or standards, ensuring interoperability becomes a significant challenge. Employing standardized encryption methods and protocols can facilitate seamless communication between diverse systems while maintaining data security across the network. Compatibility testing and protocol updates are essential for ensuring smooth interoperability.
User Training and Awareness
Oftentimes, the human element poses a challenge in data encryption efforts. Lack of awareness among users about the importance of encryption practices or inadequate training on handling encrypted data can lead to vulnerabilities in the network. Conducting regular training sessions, raising awareness about cybersecurity best practices, and emphasizing the role each individual plays in maintaining a secure network environment are essential steps to address this challenge.
Stay ahead of cybersecurity threats with encryption
As technology advances, so do the tactics used by cybercriminals to breach networks and steal sensitive data. By staying proactive and implementing robust encryption measures, organizations can effectively safeguard their information and thwart potential threats.
Data encryption serves as a powerful defense mechanism against evolving cybersecurity threats. By encrypting data both at rest and in transit, organizations can significantly reduce the risk of unauthorized access or interception by malicious actors.
Regularly updating encryption protocols and algorithms is crucial in staying one step ahead of cyber threats. By keeping abreast of the latest advancements in encryption technology, organizations can ensure that their data remains secure even against sophisticated hacking attempts.
Embracing a culture of continuous improvement and learning in the realm of cybersecurity is key to staying ahead of threats. Encouraging employees to stay informed about cybersecurity best practices and providing regular training on encryption techniques can empower them to be proactive in protecting sensitive data.
Conclusion
Data encryption is a powerful tool in safeguarding sensitive information and enhancing cybersecurity measures on networks. By implementing robust encryption methods and staying vigilant in monitoring encrypted data, organizations can significantly reduce the risk of data breaches and unauthorized access. As technology continues to evolve, so too must our approach to protecting data – let us embrace the challenge with confidence, knowing that we hold the key to a safer digital future.
ehmmzlhmqhtlgzzxhpudgeoiptdkxm